Rotary Pools for Semi-Static NAT / Port range Forwarding
Cisco routers have a very robust network address translation feature set.The NAT software allows you to control translation with access-list, route-maps, and destination pools.With the wide array of commands, it is sometimes difficult for beginners and experts to figure out how to combine these elements to solve a problem.
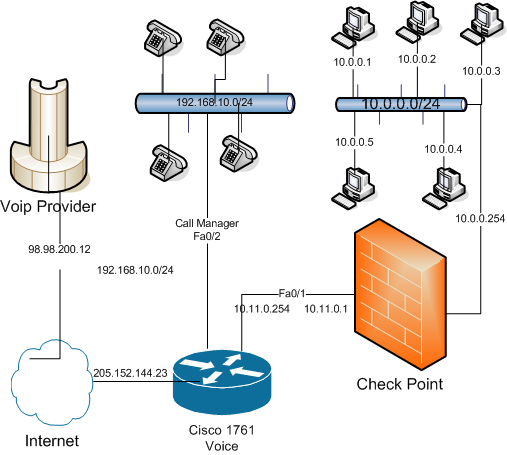
I have a small network at home for the computers in my house, and I find that some of the strangest configurations and explorations come about because I try to solve problems in a way that is cost affective with the limited broadband available to consumers.I recently purchased a CheckPoint UTM firewall appliance to add to my network.CheckPoint invented the stateful firewall and has one of the best firewalls in the market.I wanted to add this firewall to my network but I faced 2 main problems.
The first problem is that my ISP only offers 1 static IP, and my router connects with a WIC1-ADSL card.
The second problem Is that my router is also a call manager express server and therefore needs to be able to receive traffic destined for the router itself.
Notice that the outside interface of the firewall has a private IP address.This is a necessity because my ISP only offers 1 static IP and it must be assigned to the router.This is a problem if I leave my router configured the way it was with port overloading enabled, all the traffic not specifically forwarded via the router will be dropped at the Cisco which renders the inside firewall useless.
So the first thing I did was to change the following configuration from port overloading to static NAT Access-list 10
Original Configuration
ip nat inside source list 10 interface dialer1 overload
access-list 10 permit ip 10.11.0.0 0.0.0.255
access-list 10 permit ip 192.168.10.0 0.0.0.255
New Test Configuration
ip nat inside source static 10.11.0.1 interface dialer1
The problem with the above configuration is that it forwards all packets to the firewall.This means that packets from my VOIP provider destined for the call manager software on the router itself were being forwarded to the firewall.This is a big problem and one that stumped me for a while.In order to fix this problem I decided to use Destination Lists.Destination Lists allow the router to evaluate incoming connections based on an access-list and translate the packets matching the criteria to hosts in a specific pool.
The interesting thing about this technique is that you can have as many pools and destination lists as you want, which means that you can use this technique to translate ranges of ports to different hosts.I know many newbies to Cisco routers look for a port range forwarding mechanism similar to what is available on consumer home gateways and routers like those from D-Link and Linksys.The following configuration allows all ports and protocols to be forwarded to the firewall except for any traffic from the VOIP provider.
ip host sip.broadvoice.com 98.98.200.12
!
!
ip nat inside source list 10 interface Dialer1 overload
!
ip nat pool nonvoip 10.11.0.1 10.11.0.1 netmask 255.255.255.0 type rotary
!
ip nat inside destination list 101 pool nonvoip
!
!
access-list 10 permit ip 10.11.0.0 0.0.0.255
access-list 10 permit ip 192.168.10.0 0.0.0.255
!
Access-list 101 deny ip host 98.98.200.12 any
Access-lsit 101 permit ip any any
Lets take the above from the beginning.
The first line above code, hard codes the ip address of the Broadvoice server.
The second line configures the NAT for port address translation just like a normal PAT configuration.
The next line creates a rotary pool called nonvoip with the ip address ofthe outside firewall as the only IP address in the pool.
The 4th line in the configuration tells the router to check Access-list 101 and translate packets that match that access-list to the rotary pool nonvoip.
Access-list 10 is used to PAT the VOIP network And the 10.11.0.0 network which is used for the external interface on the firewall. Access-list 10 is required for nat to function.
Access-list 101 tells the router to exclude all traffic from the NAT process, but send every other protocol and port to the outside interface of the checkpoint firewall.
The above configuration can also be easily modified to forward port ranges to different hosts on the network.Once you figure out that you can have as many destination pools as you want with as many access-lists as you want the combination of port forwarding options becomes almost endless.For instance the above can be modified as follows to forward a range of ports to two different hosts.
ip nat inside source list 10 interface Dialer1 overload
!
ip nat pool groupA 10.11.0.1 10.11.0.1 netmask 255.255.255.0 type rotary
!
ip nat pool groupB 10.11.0.2 10.11.0.2 netmask 255.255.255.0 type rotary
!
ip nat inside destination list 101 pool groupA
!
ip nat inside destination list 101 pool groupB
!
access-list 10 permit ip 10.11.0.0 0.0.0.255
!
Access-lsit 101 permit tcp any any range 8000 9400
!
Access-list 102 permit tcp any any range 50 1024